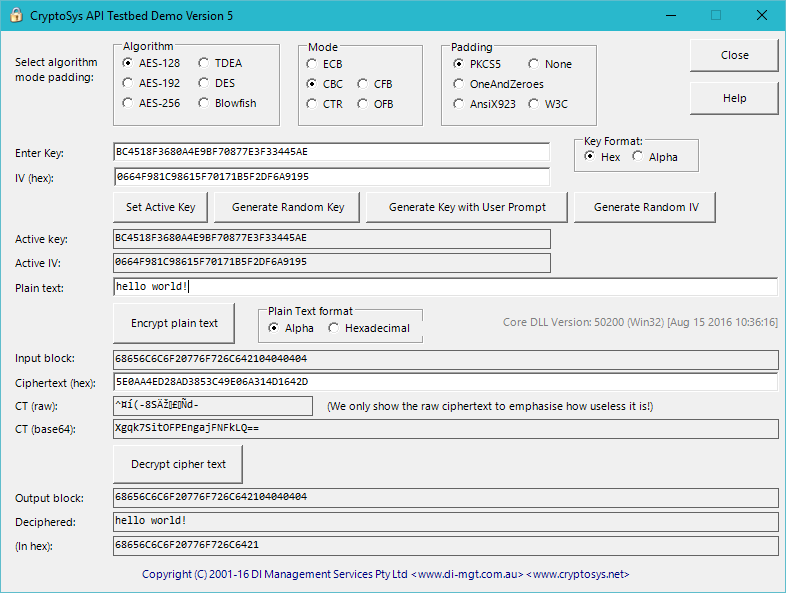
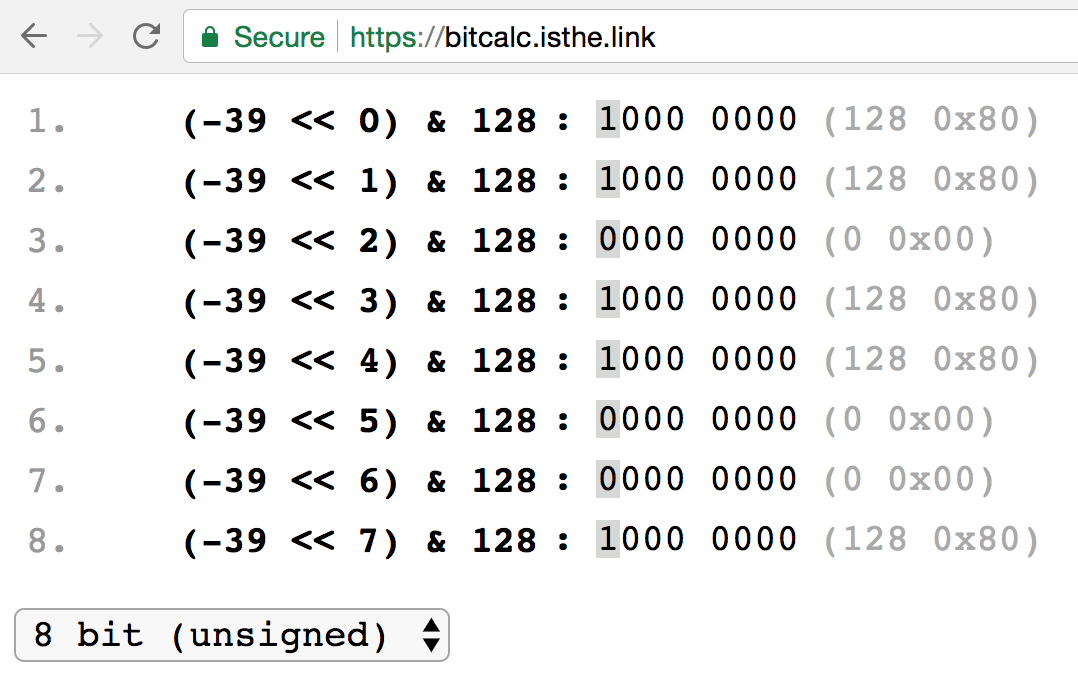
What's the deal with encryption strength —is 128 bit encryption enough or do you need more? | by Lance Gutteridge | Medium

An example of a 36-character string depicting a 128-bit binary value in... | Download Scientific Diagram

On the Properties of Bit String-Based Measures of Chemical Similarity | Journal of Chemical Information and Modeling

An example of a 36-character string depicting a 128-bit binary value in... | Download Scientific Diagram

Igor's Tip of the Week #128: Strings list - Malware Analysis - Malware Analysis, News and Indicators


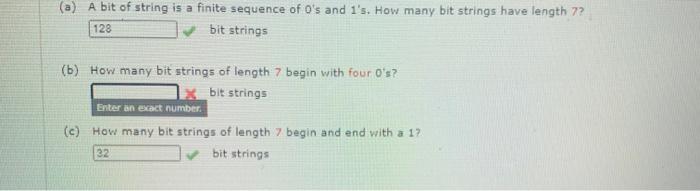




![java - String vs char[] - Stack Overflow java - String vs char[] - Stack Overflow](https://i.stack.imgur.com/WhEBr.png)